Month: December 2014
Microsoft telling the US government off
I love this debate. Imagine if this was the other way around. If a European (or for that matter any other country) asked for US based data. In my opinion, this could have terrible precedence.
Microsoft tells US: The world’s servers are not yours for the taking
http://arstechnica.com/tech-policy/2014/12/microsoft-tells-us-the-worlds-servers-are-not-yours-for-the-taking/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+arstechnica%2Findex+%28Ars+Technica+-+All+content%29
Great work by the writer on this one.
How to be personally secure in the cloud world (Part 2)
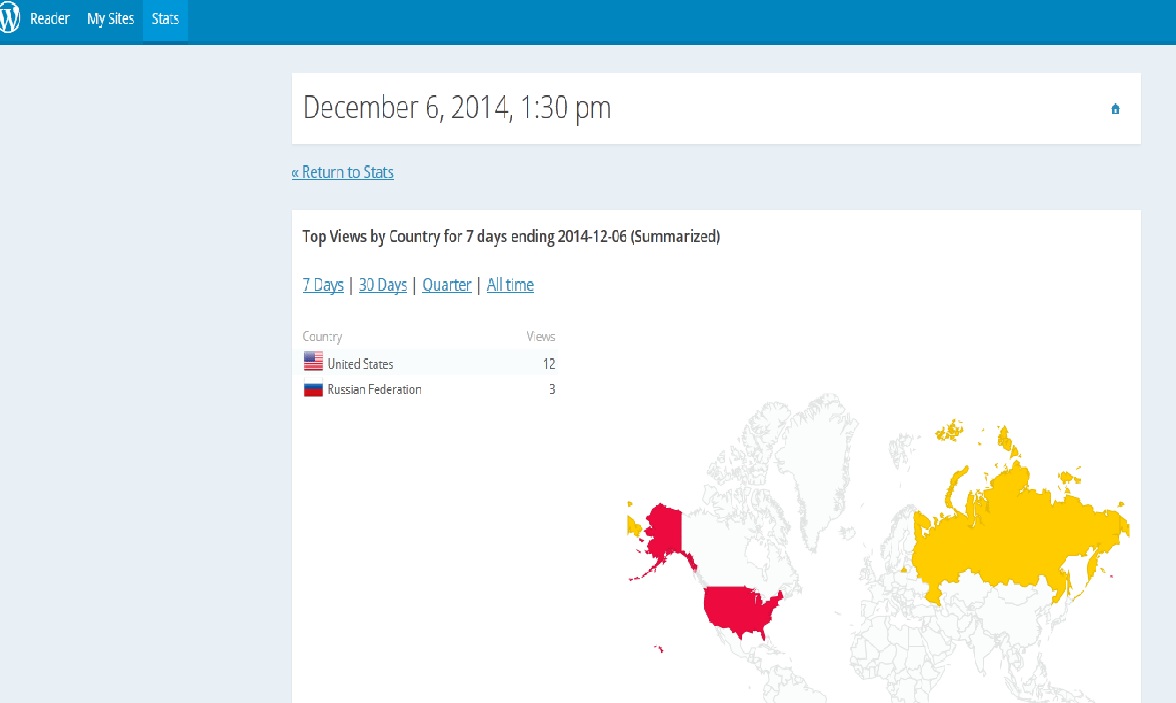
Interestingly after publishing the last blog, I started getting blog views from the Russian Federation. The image above shows the last 7 days of views, before this blog was published.
Here is part 2 of the discussion with Jeremy (Background: I recently had a chance to talk to a friend, Jeremy Guthrie, who has been in the Information Technology / Internet Service Provider business for 23 years, concentrating on networking and security architecture).
What about the tradeoffs of over-securing?
Jeremy: One of the most dangerous things you do every day is get into your car and drive somewhere. But we all do drive or use some sort of transportation daily, because of the fact that there is a risk and a tradeoff. So don’t over secure yourself so much that you hurt your online experiences substantially.
For example, let’s think about the Apple iCloud breach from this summer. Apple and other providers could have done way more to protect the information that was stolen. However, these providers also have to consider the tradeoffs of various levels of security vs. usability. For example, you can gain more security by using multi-level authentication or varying degrees of password complexity or user logouts after X number of logins. This also means it could make their cloud services difficult to use and cumbersome. So this security situation is a tradeoff between convenience and usability vs. security. If you have to attract a large user base, you have to make the product easy to use. Regardless, the provider should be transparent about how they protect their data across their entire online interface. Your choice is whether you want to leverage their additional tools to secure your data and post your data there.
My thoughts: Apple has implemented two-step verification for Apple ID, which is the user ID used with iCloud. It is not turned on by default. Here is a link to turn it on: http://support.apple.com/en-us/HT5570
Anything else we should watch out for?
Jeremy: Be careful about exchanging too much information on websites associated with different political / charitable causes. While the websites might try to secure the environment, these are generally targets for groups of hackers who want to malign the website / cause. Thus you are providing an unnecessary target on your information.
Another Interesting phenomenon currently developing is the Apply Pay feature and how it will impact your financial services. For example, before when your credit card was stolen and unauthorized transactions were made through it, the bank would help you out in most cases and take your word for it. However, now that the credit card credentials are on your phone, if it gets stolen for a certain time period before you realize the phone is stolen, will the bank hold you responsible for proving whether this item was stolen? Effectively, the phone is still authorized by you to make the payments on your behalf. And if you thought TouchID was not vulnerable to finger print spoofing, think again. The onus would shift to you to prove that the phone was stolen, in a time period when you don’t actually have your phone in your possession. Just something to ponder.
Interesting reads Jeremy recommended about security:
- Freakonomics blogs and podcasts about security offer an interesting take on security, risk aversion and the costs related to it
- Science of Fear – Why We Fear the Things We Shouldn’t–and Put Ourselves in Greater Danger by Daniel Gardner is about tradeoffs
- Spycraft: The Secret History of the CIA’s Spytechs, from Communism to Al-Qaeda by Robert Wallace is a look into how far people will go to get information.